A recent supply chain attack has affected websites using the content delivery network (CDN) cdn.polyfill.io. Polyfills are used on the web to allow content to run on older browsers that do not support current functions.
Advertisement
Polyfills map unsupported APIs so that the application can run as well as possible in the browser. The goal of the Polyfill.io project The aim is to simplify integration by providing the necessary polyfills for the respective browsers.
In recent days, several security researchers have reported malicious code distributed via Polyfill.io. Apparently more than 100,000 sites around the world are affected.
Act now!
Anyone whose web application has a dependency on the domain Polyfill.io should remove it immediately. The open source project itself is not affected, only the Polyfill.io site is affected.
 HashiCorp: New names and features for Terraform, Packer, and Vault
HashiCorp: New names and features for Terraform, Packer, and Vaultboth are fast as well as Cloudflare has been offering since February Alternatives to Polyfill.io’s CDN. The Readme is also available in German in the GitHub project There is a contradiction in the choice of domain: it declares that the project officially uses Cloudflare for CDN, but at the same time refers to the documentation on the polyfill.io website.
Warnings since February acquisition
In February, the Chinese company Funull acquired the Polyfill.io site, originally backed by the Financial Times. The operator of the Polyfill project, Andrew Bates, who works at Fastly, called on X (formerly Twitter) to immediately remove the dependency on Polyfill.io.
At the time, the discussion was ongoing on an issue of the related GitHub project, which has since been removed Still viewable at the Wayback Machine web.archive.org,
Cloudflare warned in a company blog in late February Eliminating software supply chain risks and establishing an alternative CDN endpoint. fast prompt reply for potential danger.
It was also constructed at the same time Site Polykill.iowhich is dealing with the issue but has not yet resolved the existing malicious code reports.
Malicious code found
Now, among other things, the blog of JavaScript security provider C/Side reports that cdn.polyfill.io is actively distributing malicious code. Apparently the content relies on HTTP headers, so it only activates on some mobile devices. According to the blog post Not only is the code obfuscated, but it also relies on lazy execution and other techniques to remain anonymous.
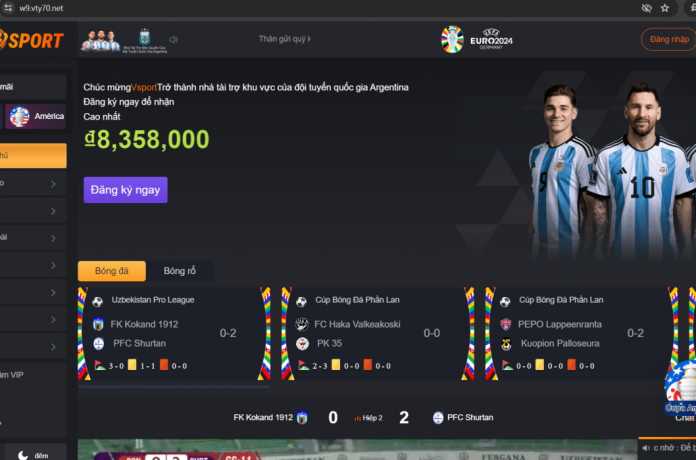
Both c/side and Sansec found a redirect to a sports betting site in code distributed via the Polyfill.io CDN.
(Image: C/Side)
Also security scanner providers Sansec warned in its blog Before the Polyfill supply chain attack. According to Sansec, Google is already blocking Google ads from sites that integrate Polyfill.io. The post also shows parts of the source code that uses a fake Google Analytics domain and redirects mobile users to a sports betting website.
(RME)
 Product Activists: The AARRR Model — How Pirate Metrics Help Product Owners
Product Activists: The AARRR Model — How Pirate Metrics Help Product Owners





