Twilio has reported that the attackers stole data from Authy accounts. This should include the telephone numbers of the affected people. The attackers, who appear online as ShinyHunters, apparently used an unsecured API endpoint for the scraping attack.
Advertisement
According to Twilio’s official announcement There are no indications that the attackers gained access to other sensitive data or internal backend systems.
App updates and the threat of SMS phishing
In the announcement, Twilio asked all users to use the latest update of the Authy app for Android and iOS. Authy is an application that generates codes for logins via multi-factor authentication (MFA). Twilio shut down the desktop version in February 2024. Since the attack took place in Twilio’s backend, questions arise about how app updates protect users.
 K 4 Premium Power Control Home Pressure Washer, by Kärcher
K 4 Premium Power Control Home Pressure Washer, by KärcherAnyone who uses the app should at least be prepared for possible SMS phishing attacks that can be used to obtain further information. As a result, SIM swapping attacks can be imagined – but the threat is very manageable in Germany. Fraudsters pretend to be a connection holder with a mobile phone operator and report the phone and SIM card as stolen in order to obtain a new SIM card with the corresponding number.
Attackers publish sample data
Security News Portal Bleeping Computer gives more details about the attack. Accordingly, a group calling itself ShinyHunters has published a CSV text file with 33 million records. In addition to account IDs and phone numbers, they contain information about the account status (account_status), the number of devices (device_count) and whether or not the devices are locked (device_locked).
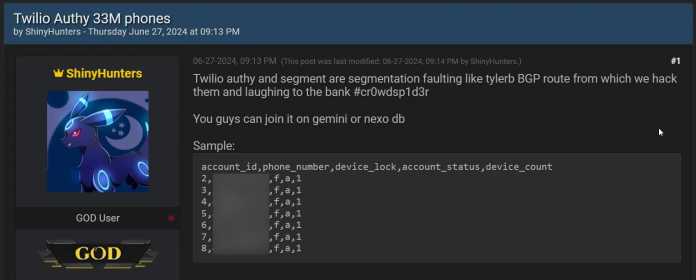
ShinyHunters shows a snippet of a CSV file with group data. Bleeping computers obscured the phone numbers in the screenshot.
(Picture: Bleeping Computer,
According to Bleeping Computer, attackers sent countless phone numbers to an unprotected API endpoint. For numbers that were in the Authy user database, the endpoint returned information about that record.
Even if the published data does not include any sensitive information such as credit card numbers, attackers at least have confirmation that a telephone number is registered with Authy through feedback from the API.
Look in the rearview mirror
This incident is reminiscent of some previous incidents: in 2019, attackers published more than 400 million phone numbers of Facebook users (now Meta). In early 2024, attackers also abused the public Trello API to link email addresses to data from Trello profiles.
Twilio was in focus in late 2022 after a phishing attack on employees resulted in attackers having access to customer data. Users of the Signal messenger were also affected by the attack.
(RME)
 Heise Online Logo
Heise Online Logo





