Supply Chain Attacks, Regulatory Challenges and New Technological Developments – In the new report “The State of Software Supply Chain,” Sonatype, a provider of applications for supply chain management, analyzed the challenges identified by more than seven million open source projects and trends. Did.
Advertisement
The number of vulnerabilities more than doubled year-on-year
With more than 6.6 trillion downloads of open source components per year and the fact that open source packages now make up 90 percent of modern software applications, developers face new challenges. The risk of malware and supply chain attacks, i.e. the introduction of malicious code, has increased over the years due to the increasing number of queries and dependencies, particularly around JavaScript (npm packages) and Python (Pypy libraries). The latter can affect code repositories, build systems, and distribution channels.
In fact, the report identified more than 512,000 suspicious packages in the OSS ecosystem last year alone, representing a year-over-year increase of approximately 156 percent over the past few years.
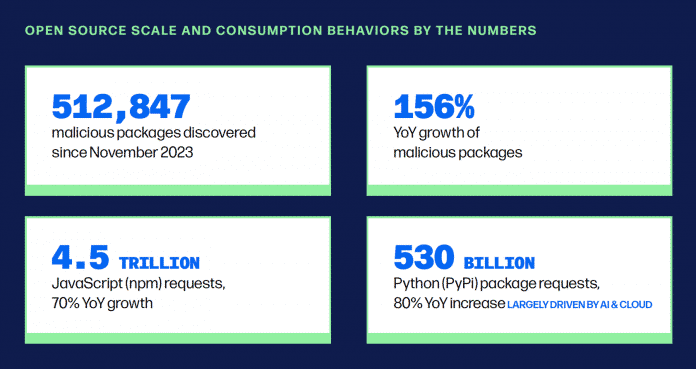
The 4.5 billion npm packages per year reflect the proliferation of open source components in the software supply chain.
(Image: 10th Annual State of the Software Supply Chain, Sonatype, 2024)
The report notes a certain inertia that prevents companies from addressing vulnerabilities. This creates persistent risks such as the Log4Shell vulnerability, where vulnerable versions of the Log4j library are still in circulation three years after they were known.
 iX Hands-On Workshop: Cloud Native Software Development with Kubernetes and Docker
iX Hands-On Workshop: Cloud Native Software Development with Kubernetes and DockerHidden risks and security concepts
The challenges faced by software development are diverse. 80 percent of application dependencies remain unpatched for more than a year, even though secure alternatives are available for 95 percent of these vulnerable versions. The fault does not lie solely with software developers. Newer versions may also come with more restrictive license terms, which should always be reevaluated for compliance reasons. Depending on the quality and clarity of the information, this may mean considerable effort.
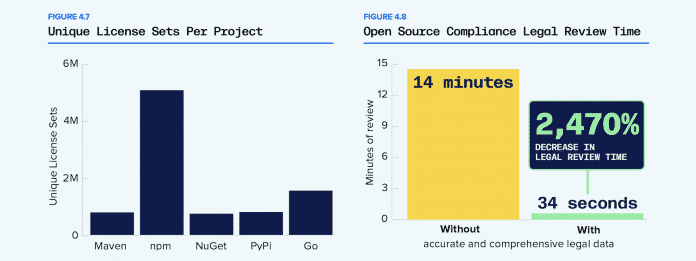
Companies will also have to consider licenses in the project. Clear information can make review easier.
(Image: 10th Annual State of the Software Supply Chain, Sonatype, 2024)
There are also hidden risks – often vulnerabilities that were rated as medium-severe in the CVSS (Common Vulnerability Scoring System) will later have to be classified as high or critical after manual assessment. Companies can quickly succumb to a false sense of security.
read this also
To address the growing risks to software supply chains, Sonatype’s analysis suggests various security concepts, particularly proactive dependency management measures.
This includes the integration of tools such as software structure analysis (SCA) into development processes and CI/CD pipelines or software bills of materials (SBOM). According to the report, projects that used such SBOM for their OSS dependencies were able to reduce their response time to security vulnerabilities by 264 days. As a provider of such devices, Sonatype also uses its own data.
The recommendations here alone will also become mandatory for some industries, for example when the Digital Operational Resilience Act (DORA) requires all financial firms to make significant efforts to increase their resilience to cyber attacks by 2025.
Report more than 60 pages Software supply chain status available for free online viewing (and also available for download upon registration) and takes into account data from over seven million viewed open source projects.
(Who)
 iX Hands-On Workshop: Cloud Native Software Development with Kubernetes and Docker
iX Hands-On Workshop: Cloud Native Software Development with Kubernetes and Docker





